Phishing protection. The illusion of security.
- Published
- 4 min reading

Alert warning: phishers ahead
The exceptional popularity of remote services and the increasing automation of many areas of life require exceptional alertness.
Along with the changing reality, the waves of threats are also changing: direct attacks give way to those carried out from afar.
These threats are:
- Rights theft
- Transaction data manipulation
- Access interception (automatic transaction)
- Identity theft (cloning of equipment)
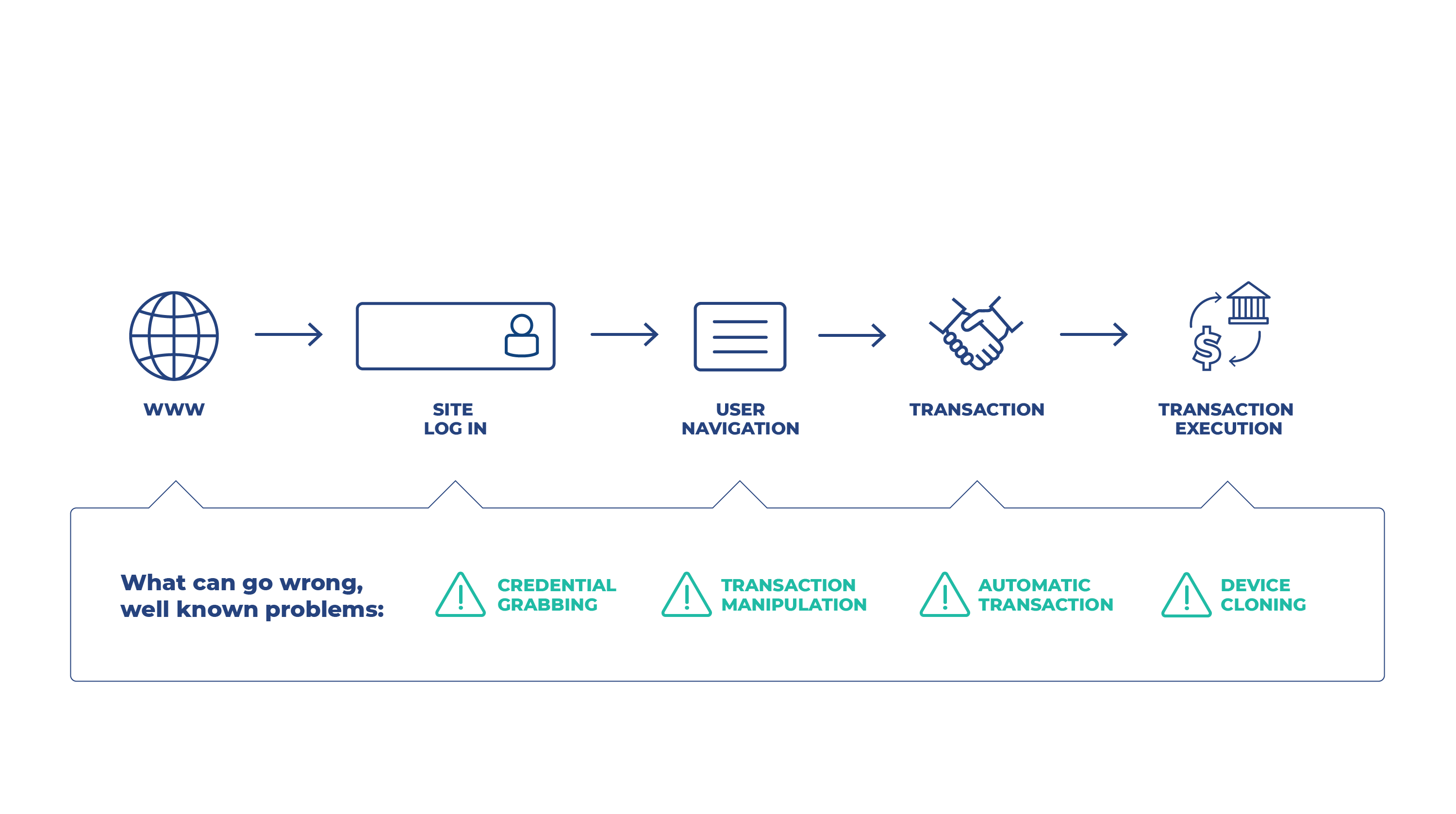
We must remember that at every stage of our interaction with the browser, something wrong can happen. It's up to us whether we're prepared for that.
The illusion of security
A few years ago, simple 2FA (2-factor authentication) tools in the form of one-time codes, scratch cards, SMS or OTP codes were brought to market. This was a step in the right direction to phishing protection, although solutions based on generating a code and then rewriting it in the browser window provide illusive security. Everything that goes into the browser window can be taken over by the hacker. An efficient hacker can also encourage us to generate a new code. Impersonating a well-known institution or shop (phishing) is a very popular, and, what is worse, still an effective method of cheating people. An email with a tempting offer from our bank or favorite shop can effectively let our guard down.
One wrong click is enough to fall victim to a fraud. The basic 2FA solutions are too weak to prevent users from losing funds or access to services.
SMS codes have a special feature. The arrival of a message informs us about the beginning of a transaction, and this fact may already give food for thought, especially when we’re watching TV, and suddenly an authorization code lands in our inbox. It’s much worse if the attack is preceded by a SIM card duplication – then the victim doesn’t quite stand a chance, because the SMS will not reach them anymore. It will however reach a cybercriminal who will use it to make a transfer on behalf of the victim.
Phishing protection. So how do we defend ourselves?
Firstly, we have to forget about passwords once and for all, because they have never provided effective phishing protection on their own. Secondly, it is important to choose the right solution for 2-factor authentication and authorization.
The most effective line of phishing defence today is formed by 2FA tools coming as hardware tokens or mobile applications (mobile token) based on PUSH notifications. The latter are very similar to SMS codes. But there is a difference – the received code does not require rewriting (so nobody can intercept it), cloning the SIM card does not give access to the user's mobile token, and the application itself may have mechanisms protecting against cloning (such as tPro Mobile).
Mobile solutions may also have a number of additional security features against phishing that analyze the runtime environment (threat detection), the way the user operates (behavioral analysis), or their location. Many available tools also guarantee the integrity of the displayed data. Thanks to this, the user can be sure that the amount and account number received in the contents of the PUSH notification are authentic (WYSIWYS mechanism).
Another family of trustworthy products are hardware tokens. Recently there’s been more and more of them, and due to their effectiveness they are becoming more and more popular (e.g. Yubiko, Titan or tPro ECC). Hardware solutions of today provide the highest possible level of security and phishing protection, mainly because they are very difficult to be targeted if one has no physical access to them. If they’re FIDO-compliant at that, they effectively protect against phishing and remote attacks, while tPro ECC also ensures the integrity of transaction data displayed to the user through the integrated CCP software (WYSIWYS).
No matter if it's a token or a mobile application – it’s prudent to think about an effective form of phishing protection today.


